Samsung Gen 3 lithium-ion battery system Q&A
2:43
In this Q&A video, Ed Spears, technical marketing manager at Eaton, introduces the Samsung Gen 3 lithium-ion battery system. Ed explains that while the system uses Samsung batteries and components, the cabinet and controls are designed and built by Eaton. Key features include a “ship complete” system with factory-installed batteries, self-powered battery management and a built-in data logger supporting a 12-year performance guarantee. Ed also addresses backup times, noting that the battery modules remain unchanged, ensuring consistent performance. Stay tuned for more Q&A videos on Eaton’s lithium-ion UPS battery offerings.
In this Q&A video, Ed Spears, technical marketing manager at Eaton, introduces the Samsung Gen 3 lithium-ion battery system. Ed explains that while the system uses Samsung batteries and components, the cabinet and controls are designed and built by Eaton. Key features include a “ship complete” system with factory-installed batteries, self-powered battery management and a built-in data logger supporting a 12-year performance guarantee. Ed also addresses backup times, noting that the battery modules remain unchanged, ensuring consistent performance. Stay tuned for more Q&A videos on Eaton’s lithium-ion UPS battery offerings.
Electrical Similar Videos
-
EV charging switchboard design and installation considerations | Eaton PSEC
9:23
Explore the design and installation of level 2 EV chargers at Eaton’s Power Systems Experience Center. Also, learn about Eaton’s EV charging infrastructure (EVCI), innovative solutions for efficient and scalable EV charging.
-
Eaton 9PX G2 UPS
0:30
Explore the enhanced features of the new 9PX G2 UPS in our latest video. https://www.eaton.com/us/en-us/catalog/backup-power-ups-surge-it-power-distribution/eaton-9px-ups/9px-g2-ups.html
-
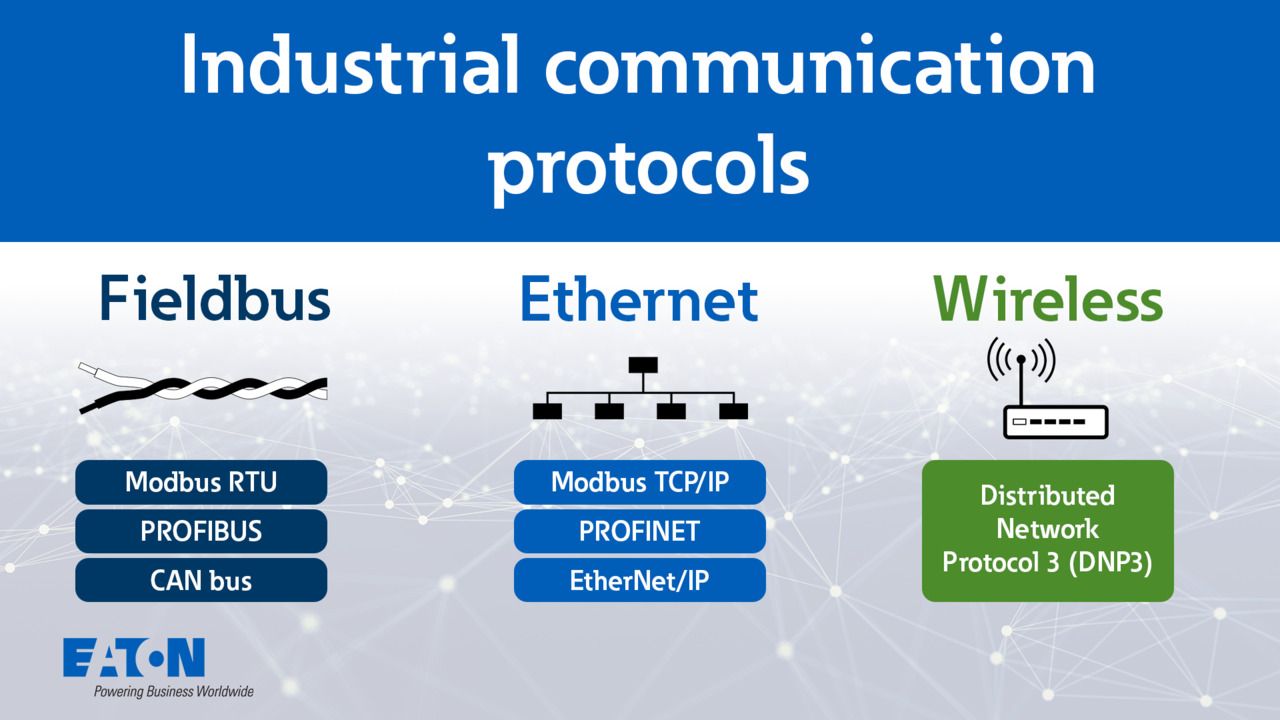
Industrial communication protocols explained | Eaton PSEC
12:23
Learn about industrial communication protocols such as Fieldbus, Ethernet, and wireless communications. Understand how they operate, their features, limitations, and cybersecurity standards.